
Low-Budget but Effective Cybersecurity
Operating a business in the modern-day world can be intimidating when we are constantly challenged with navigating an internet inundated by ransomware, malware, phishing schemes, reputation attacks, and a mélange of other sinister schemes. Small businesses and organizations are especially vulnerable to these risks, as they are often working with finite budgets, limited technical knowledge, and minimal resources to invest in software and hardware. These risks exist for almost any sized company or organization that maintains a digital footprint – whether it be a website, online forum, hosted software service, or shared cloud storage.
A cyber-attack that would otherwise be a correctable nuisance for a large company could be devastating for a small business or organization without the resources to properly recover. Being in a small business means wearing many hats and at the same time being open-minded to simple yet economical strategies to help secure online resources and intellectual property.
Networking Equipment
Many of us at small businesses don’t need to serve a large internal network or intranet, and therefore likely maintain a simple modem and router setup. Oftentimes, people opt for consumer and household-grade technologies that can be very efficient and user-friendly in terms of setting up a network, but very limiting in the scope of built-in security and monitoring. However, for a similar price-point, most companies should consider investing in small-scale business and enterprise-grade equipment.
While it takes a bit longer to set up and has a slightly higher learning curve, Ubiquiti offers a plethora of products and solutions tailored to businesses on a budget. The simple combination of a small switch, router/firewall, and access point can be integrated at a marginally higher price than mid-range home consumer-grade equipment. The tools they provide include a user-friendly network monitoring dashboard (Figure 1), a set-and-forget firewall, business-grade network resiliency, constant firmware updates, and a guest network complete with a branded logon portal.
These tools are critical to what is known as “sandboxing” and “network segregation” which every small business should be utilizing. By encouraging your guests and clients to access the guest network and login portal, you can limit any potential malware on their devices from touching your main networks. Additionally, it’s prudent to include a “terms and conditions” modal that can handle all the legal jargon and liability of having foreign devices utilizing your network connection. This equipment has been instrumental in keeping our business humming along smoothly and has successfully blocked multiple access attempts on our network already (Figure 2).
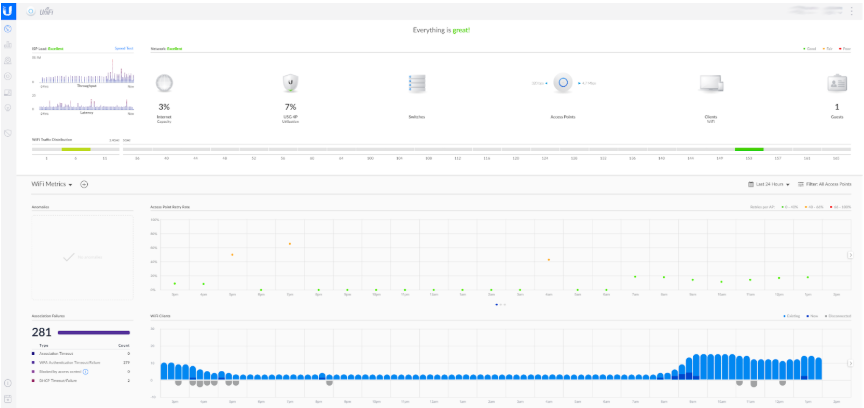
Figure 1 displaying our Unifi’s monitoring dashboard. This is a very user-friendly GUI, and a great resource for monitoring network speeds, checking logs, displaying connected devices, and troubleshooting connectivity problems in general.
![]()
Figure 2 is displaying a screenshot from our network’s live IPS logs showing a Ransomware tracker on a guest’s computer trying to initiate connection to an outside source (and likely initiate a secondary protocol). In this case the Security Gateway was able to shut down the connection before it escaped the network.
IoT Devices
One of the many topics high up on a IT professional’s list of concerns is “Internet of Things” devices. While these IoT devices provide a high level of accessibility towards handling everyday tasks, security tends to be an afterthought. Businesses should gauge whether they really need a resource to be online and highly available from outside the network. While a smart refrigerator or web application-controlled light bulb might seem like a convenient upgrade, you are opening your internal network to a new source of low hanging fruit and more attack vectors. Keep in mind these principles also apply to devices with Bluetooth and aging WPS devices, which both present easy ways into devices and your network.
In general, if you want a device to be wirelessly-accessible it is best practice to stick with hardware that has a dedicated network adapter, no Bluetooth functionality (or switched off), and accessible only from the internal network. If an IoT device is an absolute necessity, take the appropriate steps to try and secure them as best as possible (such as placing them on a separate network, selecting strong passwords, and keeping firmware up-to-date).
Password Management
Regardless of company size, password management and complexity remain two of the most easily implemented yet most-often neglected security measures. We encourage the use of well-respected password management systems, such as Lastpass. While creating and remembering long, complex passwords can be quite challenging, software such as Lastpass creates a simple solution by having a user remember only one master password, while it can simultaneously generate extensive lists of complex passwords for all your applications and store them appropriately. The unique way in which Lastpass stores the passwords also means that even if malicious parties were to get a hold of the database information, it would be indecipherable. Additionally, this also means that even the company itself is not able to view or recover your stored information, so having a strong yet easily remembered master password is critical. Brute force password attacks and offline password-matching tables remain two of the most heavily utilized entry points for hackers and malware.
Backups
One of the most prevalent forms of malicious software we hear about now in both the news and inside sources is ransomware. Ransomware is a term used to describe a variety of malware that typically encrypts databases, files, or systems in order to obtain a paid ransom. This technique is especially damaging because there is rarely a solution to decrypt the data without a master unlock decryption key, which the parties claim to provide on payment. Regularly backing up data is a necessity in general but these days the rampant occurrences of ransomware stress that even more so. The process of backing up and restoring your data should be outlined in a company’s BCP (Business Continuity Plan) which does not have to be complex but at the very least can be readily referred to in a time of crisis.
There are a host of services and solutions for regularly backing up data that don’t have to break the bank. Many of these products are cloud-based (such as Google Drive and Amazon AWS S3) and can be quite affordable for small businesses and organizations. For offline and customized plans, Acronis is a recommended top favorite for creating scheduled, user-friendly backups. For your CMS, Wordpress provides simple yet affordable ways to schedule downloadable backup and hosting platforms like WP Engine provide the same. It’s important to note that the best solution for a small business depends on many factors including the type and size of data, how often it needs to be accessed, and if you need to conform with any applicable laws and regulations (such as HIPAA and Europe’s new widely-adopted GDPR). The National Institute of Standards and Technology (NIST) also routinely release updates to Small Business Security Fundamentals that provide the foundation for our own company’s security policies. Depending on a company’s budget there are also a variety of cyber liability insurance providers that provide additional protections and financial recovery solutions in the event of an attack or breach.
In closing, you certainly don’t have to be a cybersecurity professional to implement some of the above strategies and hopefully the topics don’t come off as too intimidating. While it’s both impossible to predict the timeframe or effects of a cybersecurity incident, it helps to be cognizant of the risks that come with maintaining any kind of online presence, big or small.
Thanks for tuning in, and remember it’s never too late to start locking down some of your own company’s resources.
“In a relatively short time, we’ve taken a system built to resist destruction by nuclear weapons and made it vulnerable to toasters.”– Jeff Jarmoc, Security Consultant.
